Addressing brand impersonation, scams, and fraudulent activity across social platforms has become critical for brands. Attackers increasingly use fake profiles, malicious ads, and cloned brand pages to target users where trust is highest.
A fast and reliable strategy allows organizations to reduce customer harm, protect brand reputation, and disrupt attacker operations early. Without continuous monitoring and response, malicious content can spread in minutes.
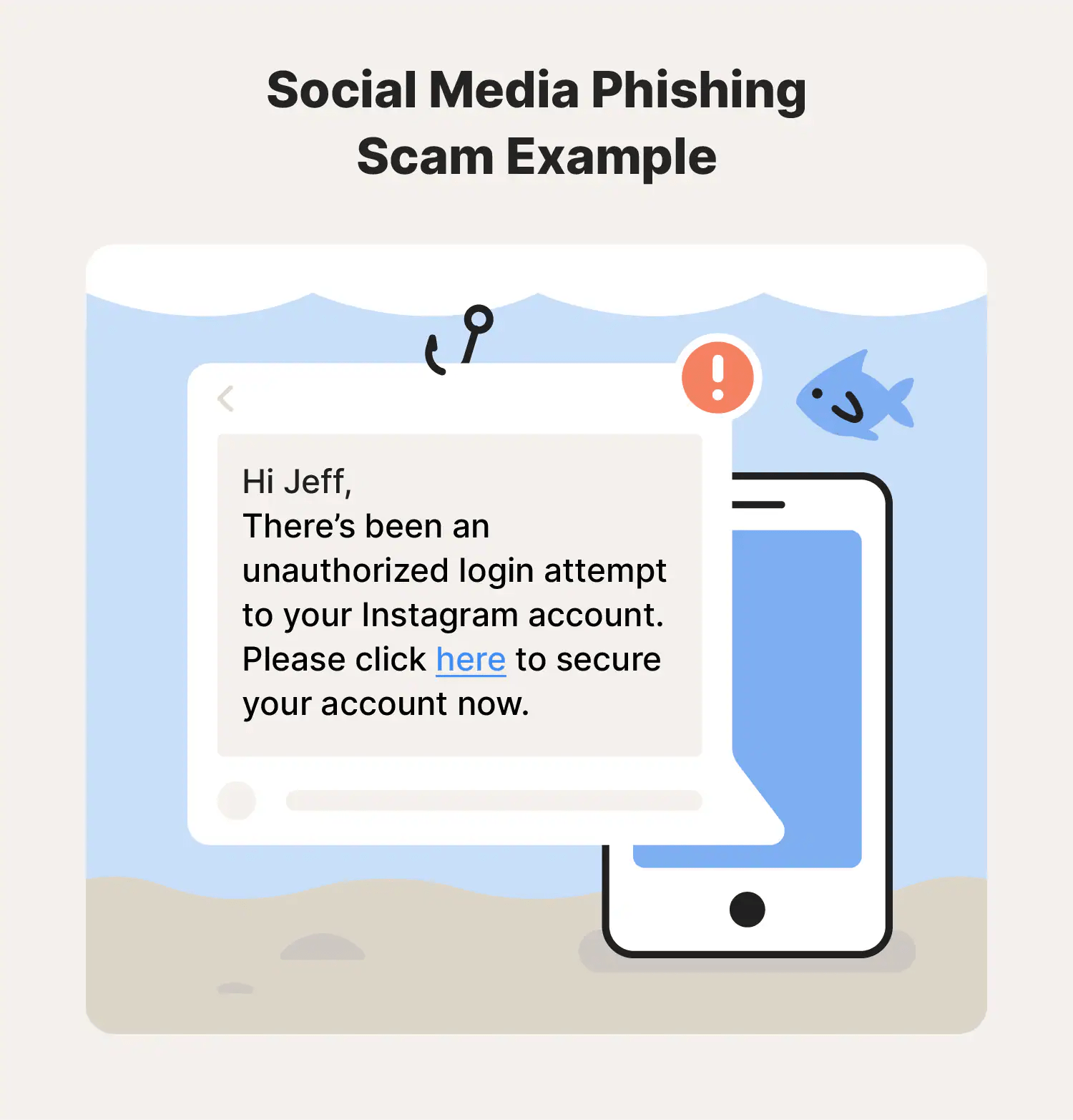
What is a social media takedown
The process of identifying and removing malicious or unauthorized content from social platforms includes fake profiles, impersonation pages, scam posts, and fraudulent advertisements.
Successful removal of harmful content requires speed, platform expertise, and accurate evidence. Attackers often rotate accounts quickly, making manual reporting ineffective at scale.
For security teams and brand leaders, addressing issues related to social platforms is no longer a reactive task but a continuous operational function.
Common threats requiring social media takedown
Fake brand accounts are one of the most common drivers of requests for content removal. These accounts copy logos, names, and content to appear legitimate.
Another major threat comes from scam campaigns using malicious links or fake promotions. These campaigns often target users directly through comments, direct messages, or sponsored posts.
Malicious advertising has also grown significantly, making timely intervention essential for stopping fraudulent ads before they reach large audiences.
Why social media takedown matters for brands
From a business perspective, protecting customers and reducing reputational damage is crucial. When users fall victim to scams, they often blame the brand being impersonated.
For a protection executive, online abuse represents both a security and trust problem. Failure to act quickly can lead to regulatory scrutiny, increased support costs, and long-term brand erosion.
Effective programs focus on early detection and rapid response rather than relying solely on user reports.
The role of DRPS in social media takedown
Digital risk protection platforms play a key role in automating workflows for content removal. Solutions like PhishFort continuously monitor social platforms for brand abuse indicators.
Once harmful content is identified, automated and expert-led workflows validate threats and submit removal requests directly to platforms. This significantly reduces the time harmful content remains active.
At scale, managing interventions becomes feasible only when automation and human verification work together.
Social media takedown and malicious ads
Attackers increasingly rely on paid social advertising to amplify scams. These campaigns bypass organic reach limits and target users with high precision.
Protection monitoring ensures that fake promotions and fraudulent ads are detected early. Combined with protection capabilities, brands can prevent malicious ads from spreading widely.
A strong removal process includes both organic content and paid ad abuse detection.
Challenges with manual social media takedown
Most major social platforms publish clear policies around impersonation, scams, and fraudulent activity, yet enforcement often requires structured evidence and persistent follow-up. Platforms such as Meta, LinkedIn, X, and TikTok outline strict rules against fake accounts and deceptive behavior, but brands still need dedicated social media takedown processes to act at scale. Understanding how these platforms handle abuse helps organizations accelerate response times and reduce the visibility of malicious content targeting users.
Manual reporting is slow and inconsistent. Platforms often require detailed evidence, and response times vary widely.
Attackers exploit these delays by creating multiple backup accounts. This makes repeated requests necessary without centralized visibility.
Organizations managing large brand footprints quickly realize that interventions must be handled systematically, not ad hoc.
Real-world social media takedown scenarios
Financial brands frequently face fake support accounts requesting customer credentials. E-commerce companies deal with scam promotions and fake giveaways.
SaaS providers often see cloned pages distributing malicious links. In each case, rapid intervention reduces exposure and customer impact.
Over time, coordinated social media takedowns also disrupt attacker infrastructure and reduce repeat abuse.
Over time, coordinated interventions also disrupt attacker infrastructure and reduce repeat abuse.
Key metrics include detection time, removal speed, and recurrence rates. Faster interventions directly correlate with reduced fraud.
Threat intelligence gathered through takedown activity also helps organizations anticipate future campaigns and strengthen prevention strategies.
Threat intelligence gathered through removal activity also helps organizations anticipate future campaigns and strengthen prevention strategies.
As social platforms continue to grow, attackers will follow. New features, ad formats, and engagement tools create fresh abuse opportunities.
This makes content removal an ongoing requirement rather than a one-time effort. Mature programs treat it as a core part of digital risk management.
Organizations that invest early in scalable capabilities are better positioned to protect users and brand equity.
Addressing brand abuse through effective measures is one of the most effective ways to stop it at the source. By removing malicious content quickly, organizations prevent scams, protect customers, and preserve trust.
Social media takedown is one of the most effective ways to stop brand abuse at the source. By removing malicious content quickly, organizations prevent scams, protect customers, and preserve trust.
With the right tools and expertise, removing harmful content becomes a proactive defense rather than a constant firefighting exercise.
Protect your brand with professional services from PhishFort