Social media impersonation has become one of the most effective tactics used by attackers to exploit trust and visibility online. From fake brand support accounts to fraudulent giveaways and investment scams, impersonation on social media allows threat actors to reach users directly, often without relying on traditional phishing links.
Unlike email-based attacks, these campaigns blend into everyday interactions. As a result, social media impersonation affects brands, public figures, and users at scale, turning social platforms into a high-risk external attack surface.
What is social media impersonation?
Social media impersonation occurs when attackers create accounts, pages, or profiles that mimic legitimate brands, organizations, or individuals. These fake accounts often copy names, logos, profile images, and posting styles to appear authentic.
Impersonation on social media is particularly dangerous because users expect to interact with brands and people directly on these platforms. This familiarity lowers suspicion and increases engagement with malicious accounts.
Common forms of social media impersonation
One of the most prevalent forms involves phishing and impersonation scams, where attackers pose as trusted brands to request credentials, payments, or personal information through comments or direct messages.
Another widespread tactic targets public figures and celebrities. Impersonators exploit large followings to promote fake giveaways, fraudulent investments, or malicious links, often reaching thousands of users in a short time.
Brands also face fake customer support accounts that respond to complaints with deceptive instructions or links, creating direct risk to customers.
How social media impersonation works
Understanding social media impersonation how these attacks unfold explains why they are so effective. Attackers begin by identifying high-visibility targets with strong audience engagement.
They then create fake accounts using similar usernames, branding, and descriptions. Once active, these accounts interact publicly through replies, comments, or hashtags, and privately through direct messages.
Because these interactions happen within trusted platforms, users often fail to recognize the threat until harm has already occurred.
Why impersonation on social media is growing
Social platforms are designed for speed and engagement, which attackers exploit. Fake accounts can gain visibility rapidly, especially when replying to popular posts or running deceptive promotions.
Impersonation on social media also benefits from low barriers to entry. Creating accounts is fast, inexpensive, and scalable, allowing attackers to reappear even after takedowns.
For brands, this results in reputational damage, increased customer support volume, and erosion of trust, even when no internal systems are compromised.
Key statistics on social media impersonation
Social media impersonation has grown steadily over the past few years, becoming one of the fastest-expanding phishing and fraud vectors. What was once considered a secondary tactic is now a primary method attackers use to exploit brand trust and user behavior across social platforms.
Industry data shows a sharp acceleration in impersonation-driven attacks between 2023 and 2025, particularly those originating on social media. Brand impersonation now represents more than half of browser-based phishing activity, reflecting a structural shift in how phishing campaigns are designed and delivered. The increasing use of automation and AI-generated content has further amplified this growth, allowing attackers to scale impersonation campaigns with minimal effort.
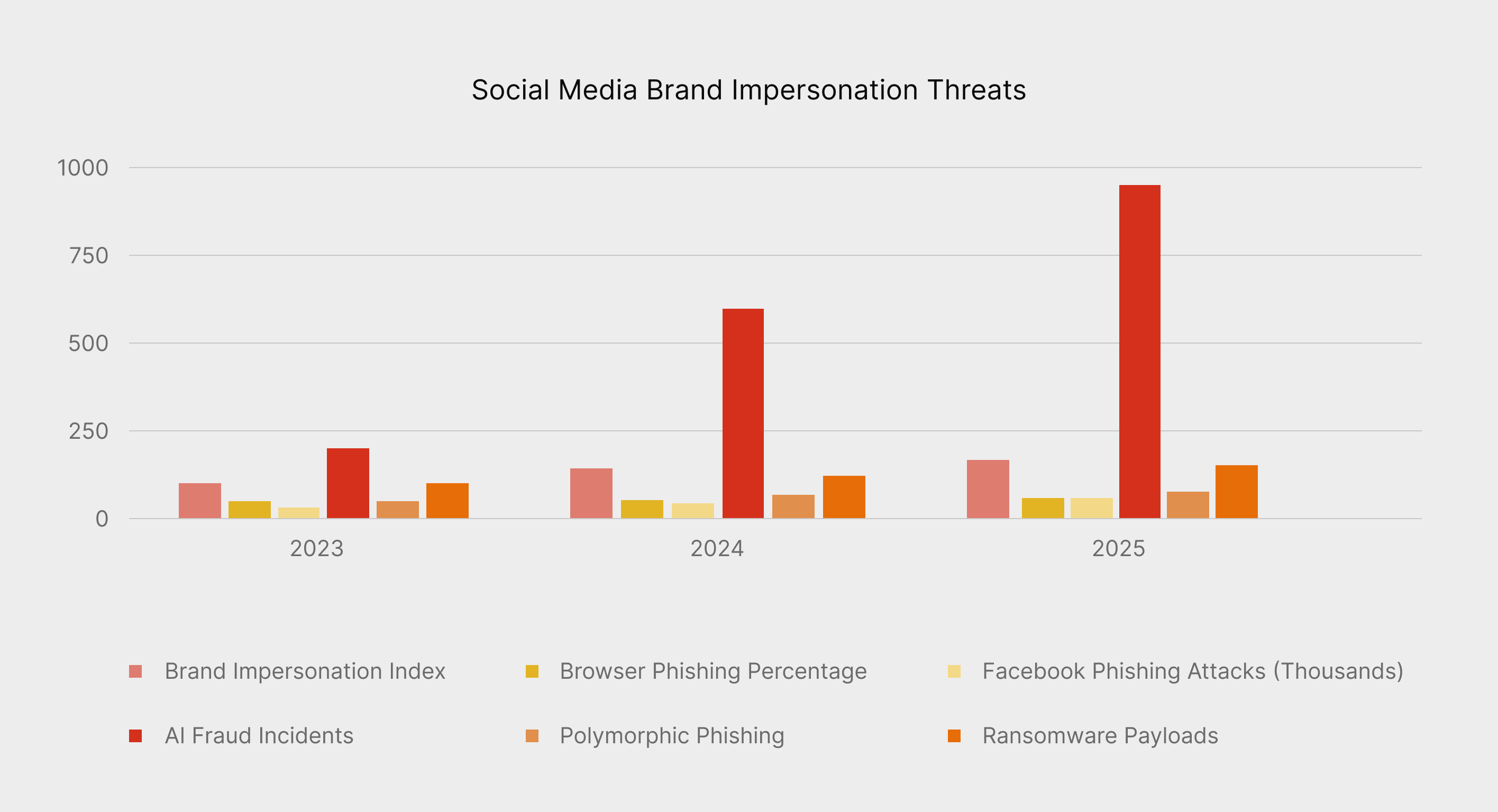
“Brand impersonation now accounts for the majority of browser-based phishing attacks, with social media playing an increasingly central role in how these campaigns reach users. This is not a short-term spike, but a sustained upward trend that continues to grow year over year.”
Source: Menlo Security
These statistics confirm that social media impersonation is no longer an emerging threat, but a persistent and expanding risk that affects brands, public figures, and users across industries.
Measuring the impact of social media impersonation
To manage impersonation on social media effectively, organizations track operational KPIs rather than relying on volume alone.
Key metrics include time to detection, time to takedown, recurrence rates, platform coverage, and user exposure windows. Faster detection and removal directly reduce exposure to scams and fraud.
For executive teams, these KPIs translate impersonation risk into measurable business impact, including reduced fraud, fewer customer complaints, and improved brand trust.
Why manual reporting is not enough
The speed and volume reflected in these metrics explain why manual reporting struggles to keep pace. Fake accounts can be created and scaled faster than platforms can respond through standard moderation channels.
As a result, impersonation on social media must be treated as an external threat surface that requires continuous monitoring and coordinated response, rather than ad hoc cleanup after user reports.
The role of digital risk protection
Dedicated digital risk protection capabilities provide visibility into impersonation activity across multiple platforms. By identifying impersonation signals early, validating threats accurately, and coordinating removals, organizations reduce how long malicious accounts remain active.
Solutions like PhishFort help brands move from reactive response to proactive control, disrupting phishing and impersonation scams before they gain traction.
Real-world social media impersonation scenarios
Financial institutions frequently face fake support accounts requesting account details from customers. Retail brands encounter impersonators promoting fake discounts and competitions. Technology companies deal with cloned profiles distributing malicious links disguised as updates or alerts.
In each scenario, early detection and rapid takedown significantly reduce customer harm and reputational damage.
Final perspective on social media impersonation
Social media impersonation exploits trust, identity, and platform reach. As attackers continue to adapt, impersonation on social media will remain a persistent risk for brands and users alike.
Organizations that invest in continuous visibility, measurable response metrics, and coordinated takedown workflows are better positioned to protect users, preserve trust, and reduce exposure to phishing and impersonation scams at scale.
Take control of social media impersonation risk
Social media impersonation requires continuous visibility and fast, coordinated response across platforms. PhishFort helps organizations detect impersonation activity early, validate threats accurately, and remove malicious accounts before they impact users or brand trust. By monitoring external attack surfaces and accelerating takedowns, PhishFort enables brands to reduce exposure to phishing and impersonation scams at scale. Learn how PhishFort protects brands across social platforms