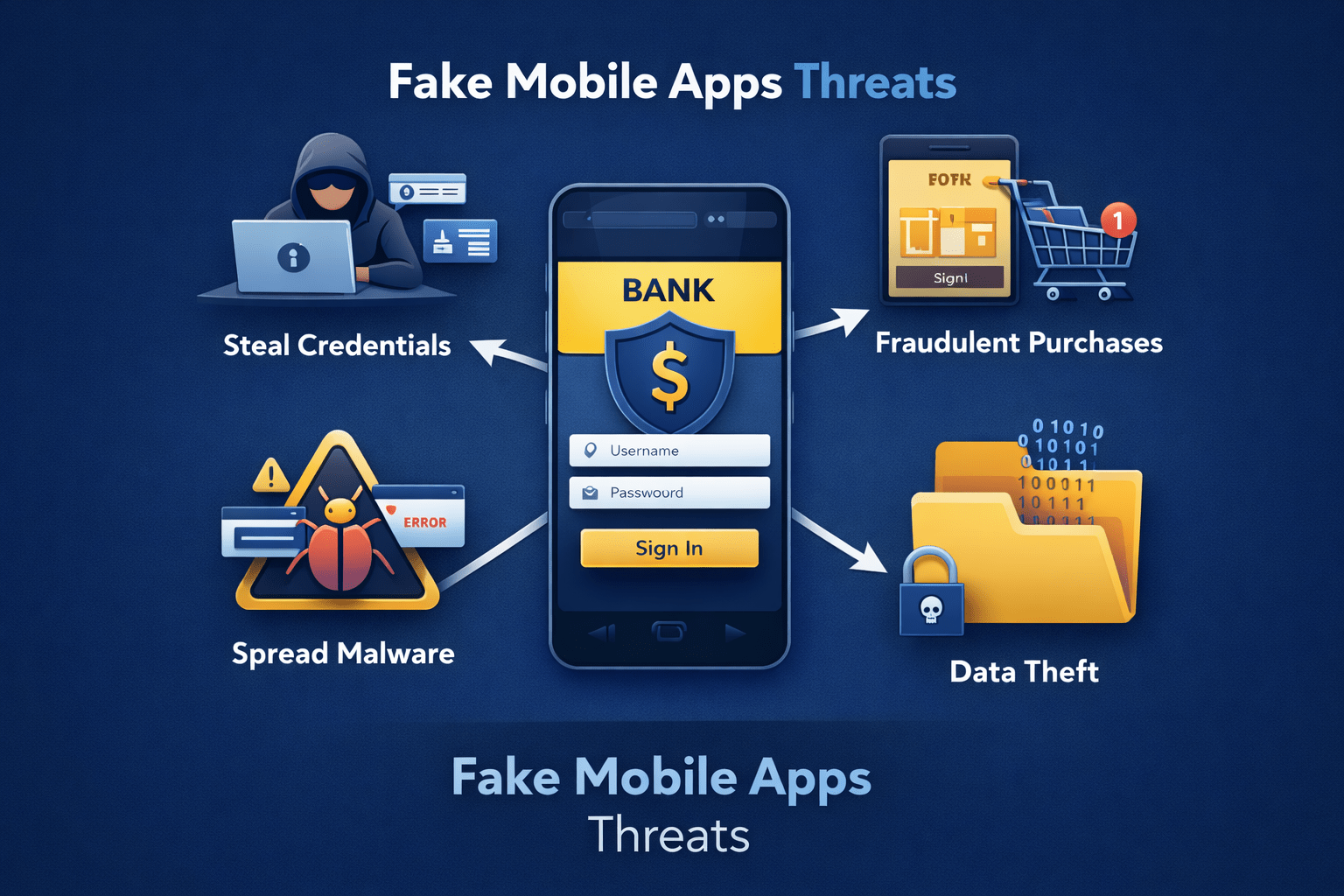
Mobile apps are a growing problem for brands and consumers alike. As mobile usage continues to dominate digital interactions, attackers increasingly rely on fake apps to impersonate trusted brands and deceive users.
These applications often appear in official app stores, making them difficult for users to identify. Without proactive monitoring, they can remain live long enough to steal credentials, harvest payment data, or distribute malware.
What are fake mobile apps
These apps are malicious or unauthorized applications designed to imitate legitimate brands, services, or products. They often copy logos, names, screenshots, and descriptions to appear authentic.
In many cases, these apps are created specifically for phishing or fraud. Attackers rely on user trust in app stores to increase installation rates and bypass skepticism.
This form of abuse is closely linked to app impersonation, where threat actors deliberately exploit brand recognition to target users at scale.
Why fake mobile apps are a serious risk
These apps represent a significant threat to mobile security because they operate directly on personal devices. Once installed, they can access sensitive data, monitor user behavior, or redirect victims to phishing pages.
Parents and guardians are especially concerned about these apps before your teen downloads them, as younger users may struggle to evaluate app legitimacy.
For brands, these apps cause reputational damage, customer support overload, and potential regulatory exposure.
Attackers publish these apps through both official and unofficial app stores. They optimize listings using brand keywords, attractive screenshots, and misleading descriptions.
Attackers publish fake mobile apps through both official and unofficial app stores. They optimize listings using brand keywords, attractive screenshots, and misleading descriptions.
Some campaigns use social media ads, malicious links, or SMS messages to drive downloads. Once installed, these apps may prompt users to log in, update payment details, or grant excessive permissions.
Understanding how attackers create and distribute these apps is essential to stopping them early.
How to spot and stop fake mobile apps
Learning how to spot these applications starts with understanding common red flags. Poor reviews, recent publication dates, and mismatched developer names often indicate risk.
However, manual detection does not scale. This is why organizations rely on digital risk protection platforms to continuously scan app stores for these applications impersonating their brand.
Solutions like PhishFort monitor app stores globally, identify suspicious listings, and coordinate takedown requests with platform operators.
The role of DRPS in fake mobile app protection
Traditional security tools focus on internal systems, not external marketplaces. These applications exist outside corporate infrastructure, making them invisible to many defenses.
Digital risk protection services extend visibility to mobile ecosystems, detecting these apps early in their lifecycle. Automated analysis combined with human verification reduces false positives and accelerates removals.
This approach minimizes user exposure and limits the operational window attackers rely on.
Financial institutions face these apps that imitate banking or payment services to steal credentials.
Financial institutions face fake mobile apps that imitate banking or payment services to steal credentials.
Retail brands see shopping applications promoting discounts that lead to fraudulent checkout pages.
SaaS providers encounter applications designed to harvest enterprise login credentials, often preceding account takeover attempts.
In every case, rapid detection and removal of fake mobile apps reduces customer harm and brand damage.
Why fake mobile apps require continuous monitoring
Fake mobile apps are not a one-time issue. Attackers frequently re-upload apps under new names or developer accounts.
As app stores expand globally, these applications appear across regions and languages, increasing complexity for brand protection teams.
Continuous monitoring ensures that new applications are detected as soon as they appear, rather than after user reports.
Final perspective on fake mobile apps
These apps exploit trust in mobile ecosystems and brands. Without proactive detection and response, these threats scale quickly and cause real harm.
By investing in visibility across app stores and fast takedown capabilities, organizations can significantly reduce risk from these applications and protect users in an increasingly mobile-first world.