Takedowns are a common part of the internet today, especially for those dealing with a compromised site. Companies and individuals regularly seek to have harmful or unauthorized content removed, but the process is rarely straightforward. As a victim, the goal is binary: is the offending content gone or not? As practitioners, we know the answer is incredibly nuanced.
While the outcome is black-and-white, getting there requires navigating a grey area of jurisdictions, policies, and technical details. The right path depends on the type of abuse and the entities involved.
(This article is part of our The Nuance of Takedowns series.)
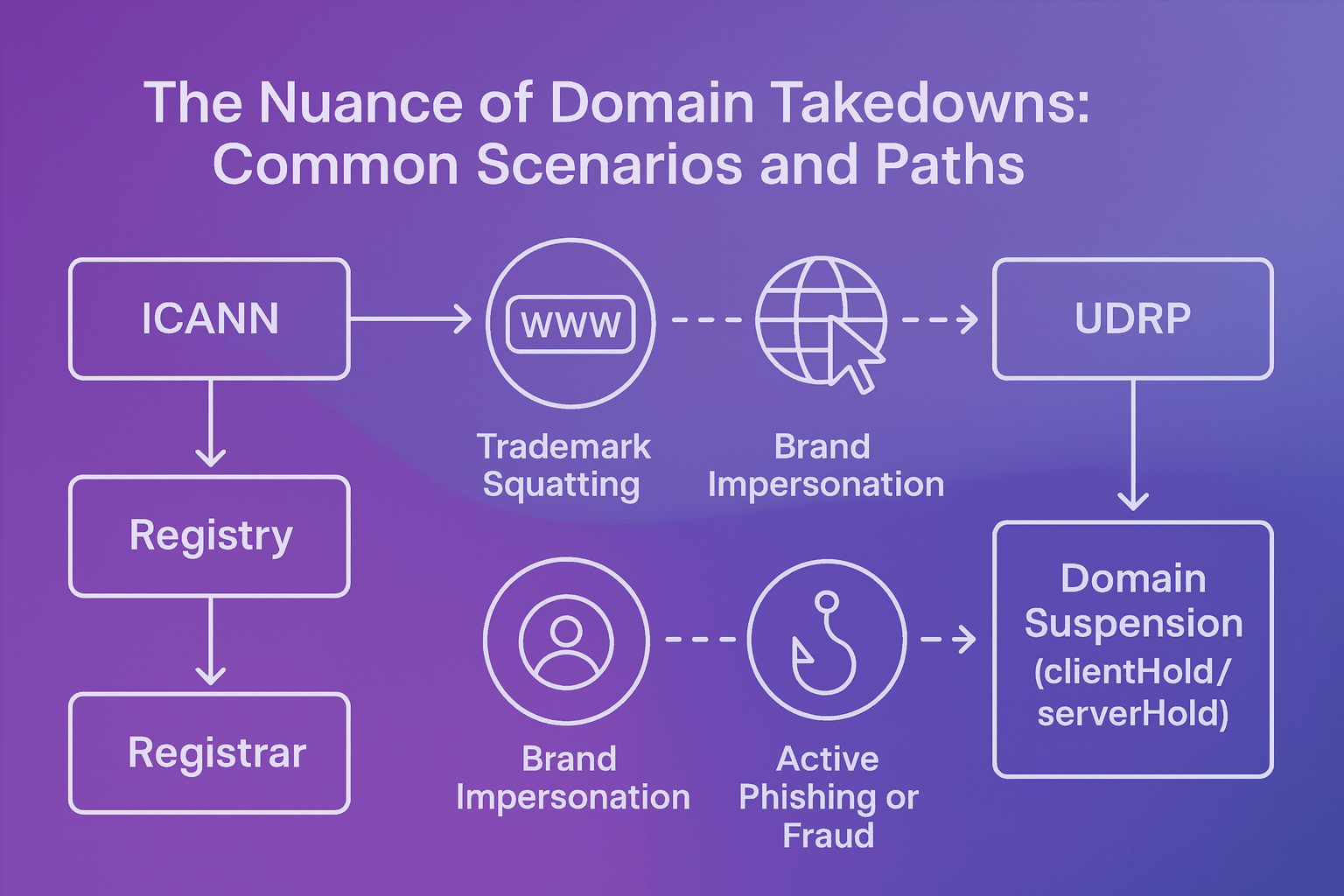
For this article, we are going to focus primarily on the registrar, registrant, hosting provider, and victim as registries will often defer to the registrar to mitigate the action first.
The Problem of Intent vs. Action
Registrars and registries are bound by their agreements with ICANN to take “prompt, appropriate mitigation action” upon receiving evidence of DNS abuse. However, the definition of “appropriate” is the source of much friction. Registrars must balance the need to stop abuse against the risk of causing collateral damage to innocent parties.
When a domain is used for phishing or malware, it is classified as DNS abuse, obligating the registrar to act. However, the decision to suspend a domain hinges on a critical distinction: Was the domain registered for abuse, or was it a legitimate site that was compromised by abuse?
- Malicious Registration: The domain was created solely for malicious activity. The intent is bad, the action is bad. Suspension is the correct tool.
- Compromised Domain: The domain is a legitimate business asset (often over a year old) that has been hacked. The owner’s intent is legitimate, but the current action is malicious.
This distinction is vital because a registrar’s primary tool, a suspension of the domain in the domain name system, is a blunt instrument. They cannot remove a single malicious file; they can only take the entire domain offline.
The “Nuclear Option”: Why Registrars Hesitate
Suspending a compromised domain with a hold is like burning down a house to kill a spider.
Because registrars operate at the second-level domain level (e.g., example.com), a full suspension (clientHold) cuts off access to everything associated with that domain. This includes the legitimate website, the company’s email servers, and any subdomains.
If a hacker plants a single phishing page at example.com/wp-content/login.php, suspending the domain example.com would stop the phish, but it would also shut down the victimized company’s ability to do business. This constitutes disproportionate harm.
Consequently, when a registrar identifies a site as “compromised” rather than “maliciously registered,” they will almost always refuse to suspend it. Instead, they shift the responsibility to the party that can use a scalpel rather than a sledgehammer: the hosting provider or the site owner.
Why Compromised Sites Are Hard to Suspend
The core difficulty in taking down a compromised site is the registrar’s conservative risk posture.
- The “Established Asset” Defense: Registrars are terrified of liability. An aged domain is considered a valuable, established asset. Suspending it creates a massive commercial risk that often outweighs the harm caused by the phishing attack it is hosting. To avoid litigation and PR nightmares, the bar for suspending an aged domain is set incredibly high.
- The Burden of Proof: The system favors the domain owner. For older domains, the assumption is that the site is legitimate until proven otherwise. To get a suspension, the reporter must prove that the domain has been taken over or was always malicious—datapoints that are difficult to obtain. If a domain has a long history, the registrar will default to preserving it.
- The Wrong Tool for the Job: As noted above, this issue gets reframed as a content issue, not a domain issue. The malicious content is a rogue script residing on a server. The entity with the technical ability to remove that file without killing the domain is the hosting provider, not the registrar.
The Role of Domain Age
Domain age is the primary signal registrars use to distinguish between a “burnable” malicious domain and a “protected” compromised one.
- Newly Registered (< 2 weeks): The industry generally accepts that these were created for abuse. Suspension is low-risk and the preferred outcome.
- Aged Domains (> 1 year): These are presumed to be compromised legitimate assets. Suspension is high-risk. The preferred outcome is content removal by the host.
This creates a distinct pivot in strategy. If the domain is new, target the registrar. If the domain is old, target the host.
Takedown Strategy for Compromised Sites
Since the goal is to remove the malicious content without destroying the legitimate business, the strategy for a compromised site must pivot away from a domain-level suspension.
- Identify and Contact the Hosting Provider The hosting provider controls the files on the server. Unlike the registrar, they can delete the specific malicious file (e.g., login-reset.php) while leaving the rest of the website online. If the content involves a copied login page or brand assets, sending a DMCA takedown notice to the host is often the most effective legal lever.
- Contact the Business (Victim) Directly Sometimes the fastest solution is to alert the victimized company. Using a contact form or “abuse@” email address found on their site can alert their IT team to the breach. Note: There is a risk that the attacker has control over the victim’s email or infrastructure. Proceed with caution and consider this a parallel step to contacting the host.
Conclusion
The nuance in taking down a compromised site lies in correctly identifying the responsible entity. When a site is compromised, the domain itself is a victim, and its registrar will be reluctant to punish the legitimate owner. The effective solution is almost always to target the malicious content and its hosting provider, thereby removing the threat while protecting the original domain owner. Understanding this distinction is a crucial diagnostic skill for a successful abuse mitigation strategy.
Contact the experts at PhishFort to learn how we can help protect your brand online
FAQs
A compromised site refers to a website that has been hacked or infiltrated, resulting in unauthorized access or control. This can lead to data breaches, malware distribution, or changes to the site’s content without the owner’s consent.
A compromised website means that it has been hacked or infiltrated by unauthorized individuals, leading to potential data breaches, malware distribution, or the manipulation of the site’s content.
Yes, compromised often means hacked, indicating unauthorized access or breach.
Website blocked due to compromised means that the website has been identified as unsafe or hacked, leading to a block by search engines or security software to protect users from malicious content.