The PhishFort Blog
Cybersecurity
Blog categories

Cybersecurity
5 min read
Social Engineering: The 'Can You Hear Me?' Trap Explained
In the high-stakes ecosystem of Web3 and venture capital, understanding social engineering is crucial as meeting …
Cybersecurity
5 min read
The Nuance of Takedowns: The Challenge of the Compromised Site
Learn the effective domain takedown strategy for all abuse scenarios: from brand squatting to active phishing. …
Cybersecurity
5 min read
Typosquat Protection in Depth: How Brands Stop Domain Abuse and Supply Chain Attacks
Typosquat protection helps brands detect lookalike domains and prevent phishing. Discover how Typosquat Protection …
Cybersecurity
5 min read
Digital Risk Protection Services Explained: 7 Powerful Ways to Reduce External Threats
Digital risk protection services help organizations detect and remove external threats targeting brands and users. Learn …

Cybersecurity
5 min read
Fake Social Media Profile Risks: How Brands and Users Get Impersonated
A fake social media profile can be used for scams, impersonation, and fraud. Learn how these profiles work and why they …
Sign up for our newsletter
Join our insider list for early access to product launches, industry insights, and expert tips.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Blog
Latest posts
Your latest source for stories, research, and updates from Phishfort.

Cybersecurity
4 min read
DRPS Tools Explained: 7 Powerful Ways to Stop Digital Threats Fast
DRPS tools help organizations detect, monitor, and remove online threats in real …

Cybersecurity
3 min read
Fake Domain Exposed: 7 Critical Risks Brands Can't Ignore
Fake domain threats are rising fast. Learn how fake domains are created, …

Cybersecurity
4 min read
The Nuance of Takedowns: A Complete Guide to Domain Suspension, Website Verification, and Takedown Actions
The Nuance of Takedowns is the title of a series created to highlight a reality …

Cybersecurity
3 min read
8 Ways Attackers Use Modern Phishing Techniques — And How to Detect Them
Modern Phishing Techniques explained through 8 examples, including clone …
Cybersecurity
6 min read
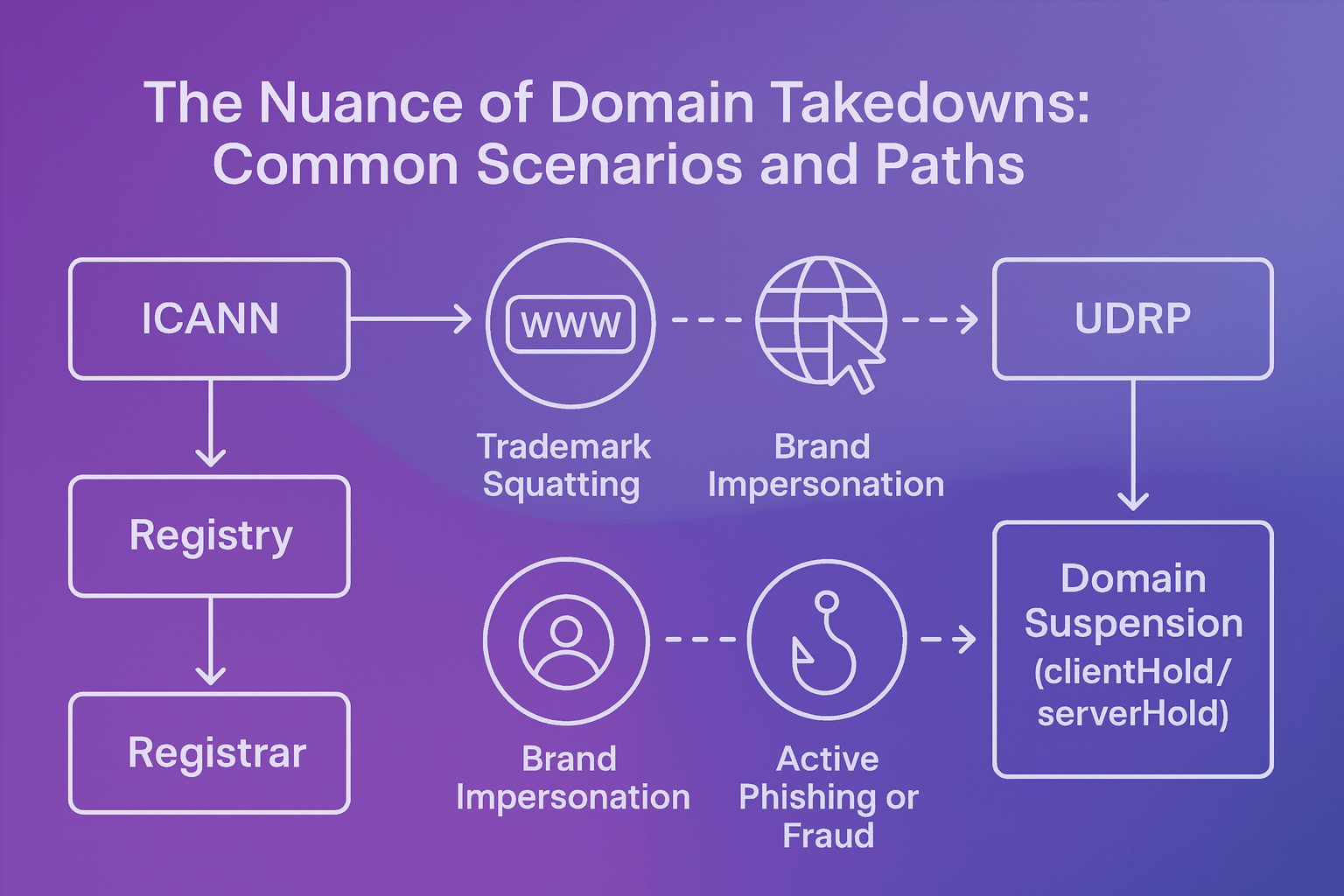
The Nuance of Domain Takedowns: Common Scenarios and Paths
Learn how domain takedowns really work—from UDRP and DMCA to DNS abuse. See …
Cybersecurity
4 min read
See in the Dark: Announcing PhishFort’s Dark Web Monitoring
PhishFort’s Dark Web Monitoring detects leaked credentials and hidden risks. …

Cybersecurity
3 min read
DMCA Takedown Process: Mastering the Steps to Success
This guide will walk you through what a DMCA takedown process consists of, why …

Cybersecurity
5 min read
The Ultimate Guide to DMCA Takedown Requests
This guide will walk you through what a DMCA takedown process consists of, why …