Threat Monitoring That Never Stops
PhishFort's global scan infrastructure continuously monitors for phishing, impersonation, and scam threats across the web, app stores, and social platforms, even years after the first takedown, ensuring attackers don't come back.
Why Persistent Monitoring Matters
Threat actors don't give up after the first takedown. Domains are re-registered. Apps are re-uploaded. Social impersonators come back under new names.
PhishFort's monitoring infrastructure is designed to prevent repeat attacks by tracking re-emergence attempts long after an incident is resolved. We don't just find threats, we stay on top of them.
With scanning infrastructure that spans the web, mobile ecosystems, social networks, and even dark web forums, PhishFort provides always-on visibility into how attackers evolve and ensures you're protected from the same threat twice, thrice, and beyond.
Threat Monitoring Keeps Attackers At Bay
While other brand protection vendors take a snapshot of threat activity, we run a live feed. We ensure that threats do not re-emerge and redirect attacker attention elsewhere.
Global Scan Infrastructure
We run continuous crawlers across DNS zones, WHOIS records, phishing archives, app stores, and social platforms to surface new and re-emerging threats.
Long-Term Watchlists
Once a threat is detected, whether it's a domain, app, or impersonator, we add it to our persistent watchlist, tracking for reactivation or clone behavior.
Re-Detection and Auto-Takedown
If a previously removed threat resurfaces, PhishFort automatically flags it, re-validates it, and re-launches the takedown process with no manual input needed.
Behavioral Monitoring and Infrastructure Clustering
Using LLMs and machine learning, we track attacker behavior over time by clustering related infrastructure and surfacing evolving scam patterns.
Complete Digital Risk Protection — Wherever Threats Emerge
PhishFort detects and eliminates digital threats to keep your brand and customers safe across all corners of the Internet.
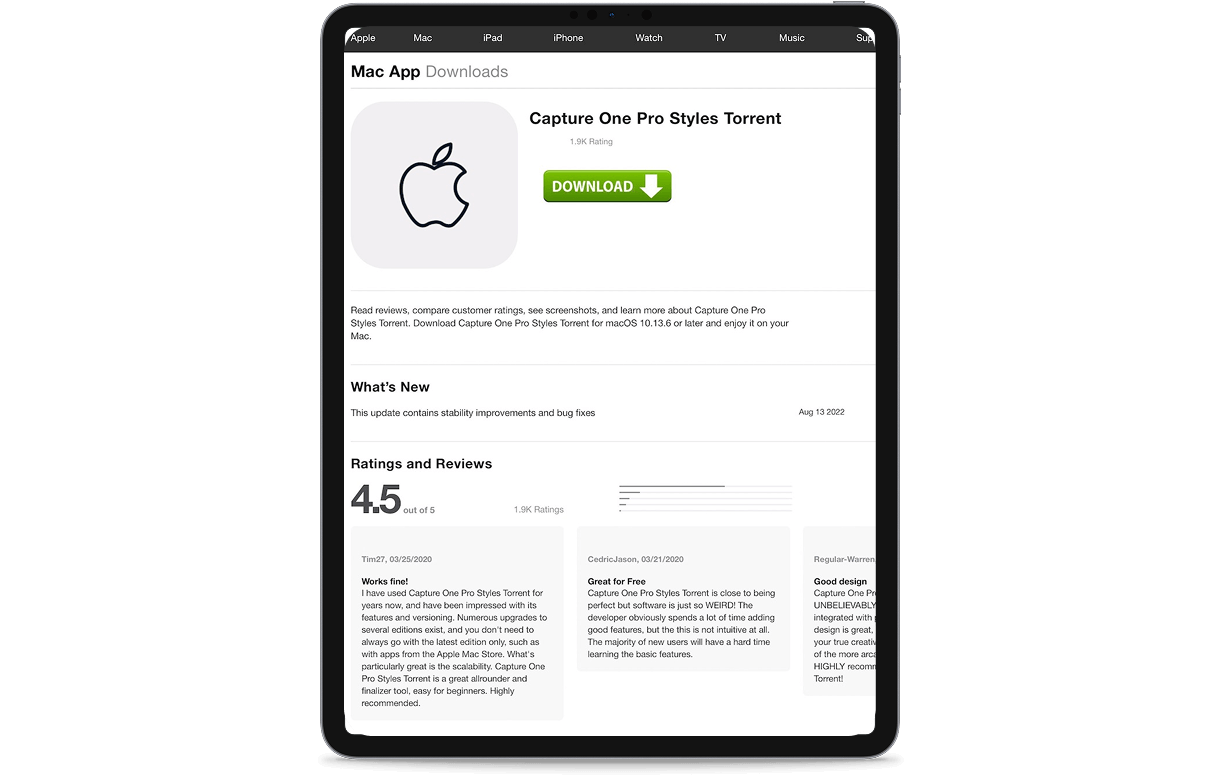
Phishing Site Detection & Takedown
Rapid takedown of fake websites impersonating your brand with 99%+ success rate.
Fake App Detection & Removal
Identify and remove unauthorized or malicious apps on Apple and Android stores.
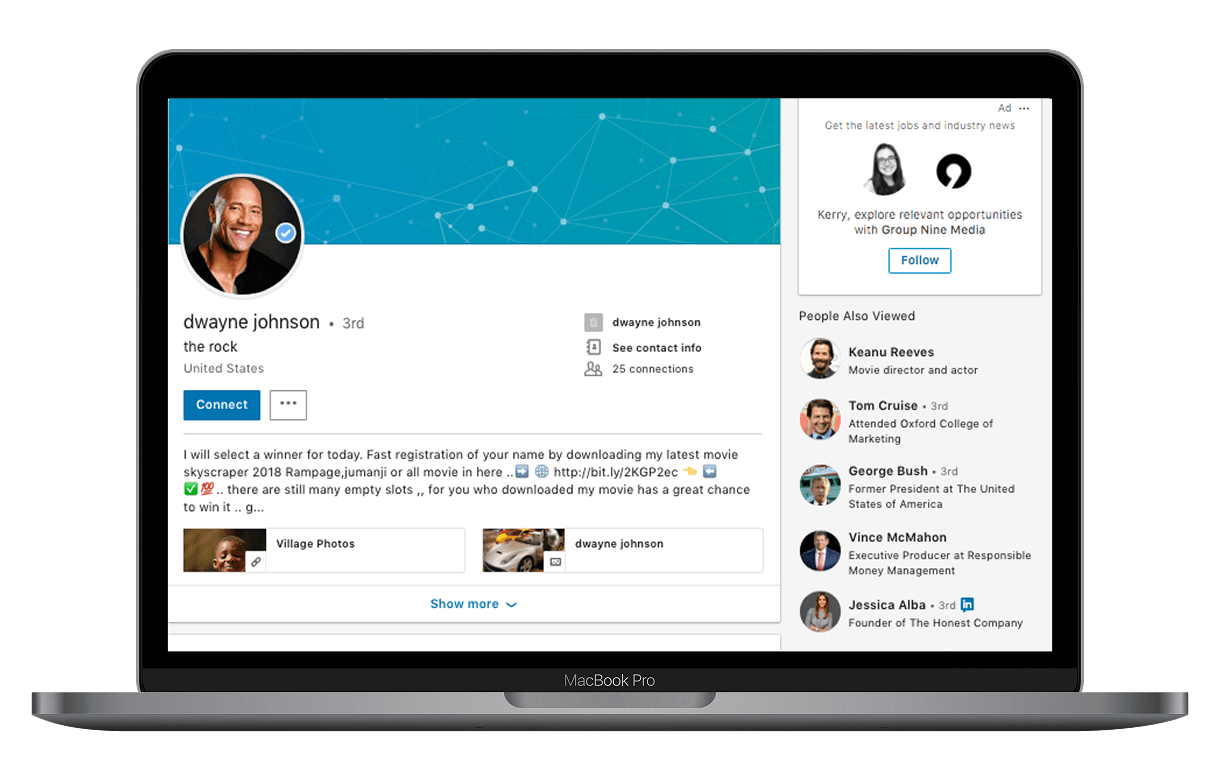
Brand Impersonation Monitoring
Detect, monitor, and remove fake profiles, bots, and brand impersonations across major social platforms.
Threat Intelligence & Monitoring
Stay ahead of underground threats—our researchers track deepfake, scam, and credential abuse activity.
Visibility You Can Count On, Every Day
Every verified threat PhishFort detects and removes is added to our continuously updated Global Blocklist a feed of phishing domains, scam infrastructure, fake apps, and impersonations used by over 418 million users.
Persistent Watchlists
Every verified threat is monitored long after the first takedown—ensuring it doesn't quietly come back.
Private Escalation Channel
Get instant alerts when legacy threats resurface, along with real-time comms with our analyst team.
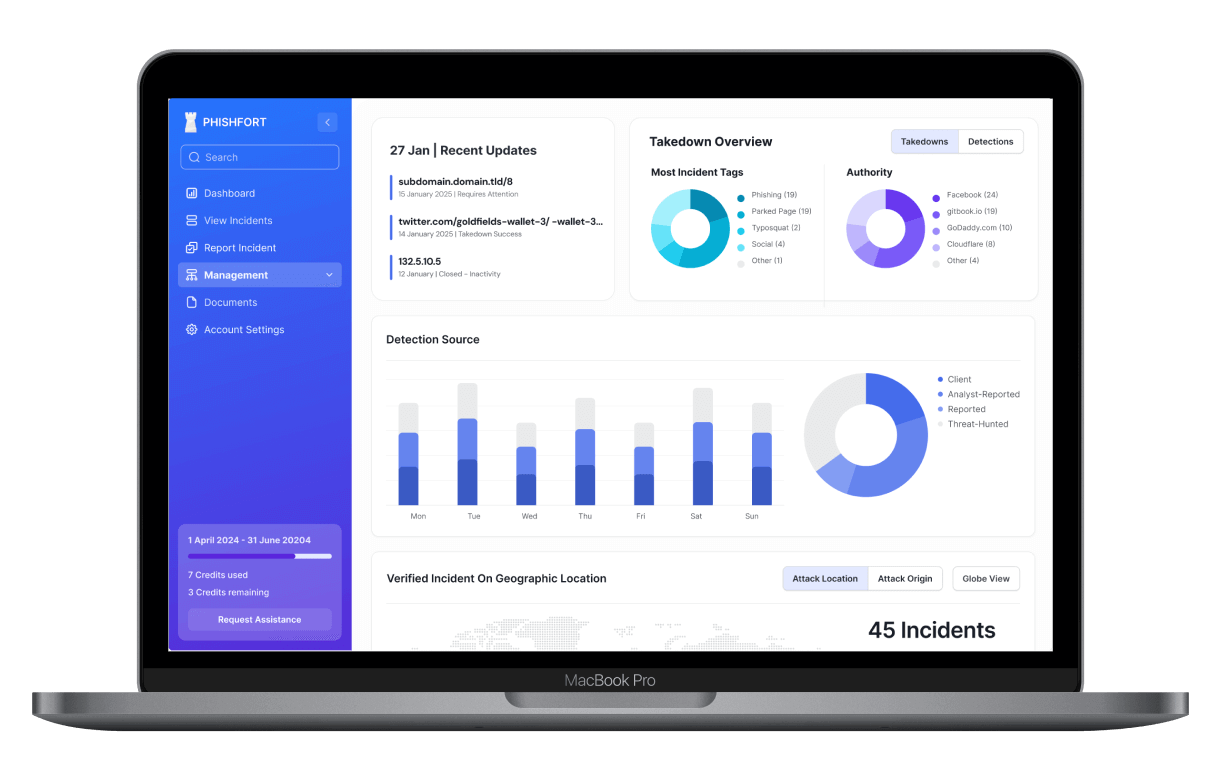
Integrated Dashboard
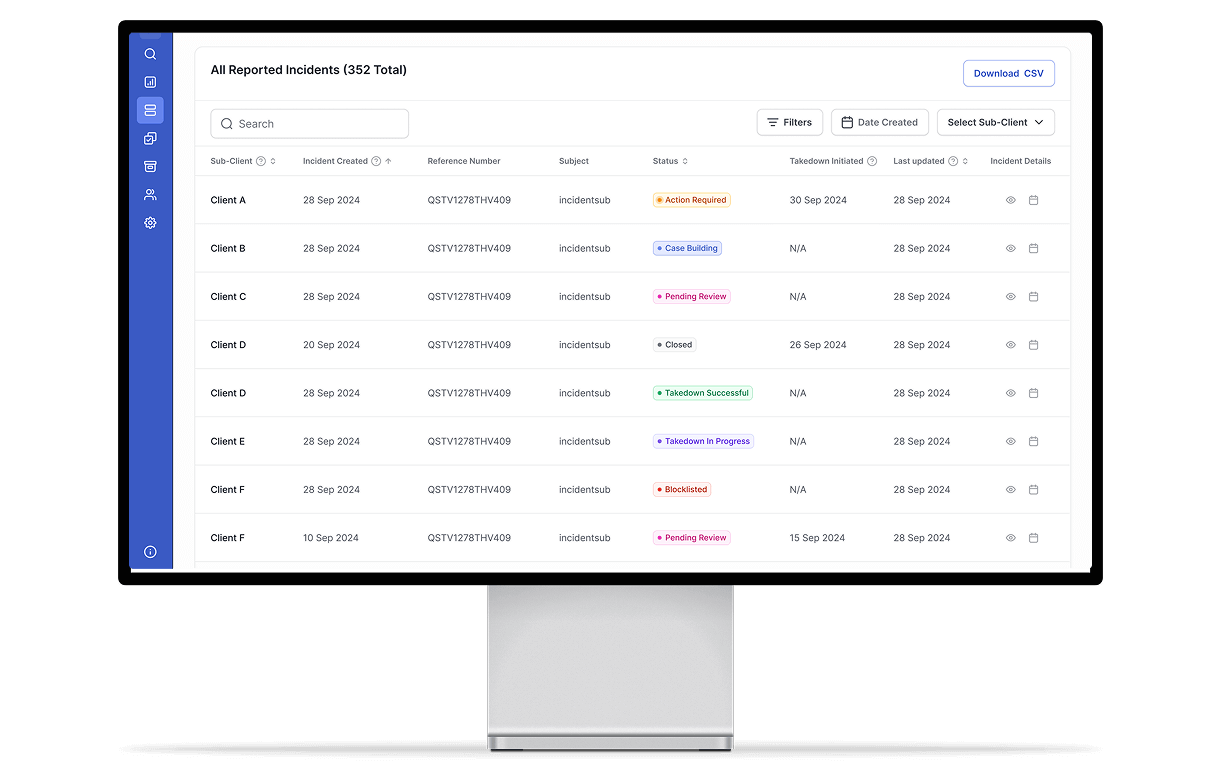
View live monitoring results, alert timelines, and threat reappearance history with full export and audit trails.
Persistent Monitoring, Proactive Defence
<p>PhishFort delivers monitoring of your brand online to ensure that threat actor activity is disrupted and their attention is turned elsewhere.</p>
Why Leading Brands Trust PhishFort
PhishFort goes beyond detection—offering everything needed to eliminate digital threats at scale.
The Gold Standard in Takedown
98%+ success across web, mobile, and social threats.
AI-Powered Threat Detection
Real-time identification of evasive, cloaked, and AI-generated threats.
Protection Across All Edges
Web2, Web3, DeFi, and beyond—PhishFort covers it all.
Low-Touch Integration
Easy setup, SOC/SIEM-friendly, and fully managed service.
Beautiful Visualization & Reporting
Intuitive dashboards, real-time alerts, and exportable reports for every incident.
24/7/365 Coverage
Always-on monitoring and live chat support when you need it.

Why Customers Chose PhishFort Above the Rest
Seamless Client Communication and Tools for Enhanced Security
Private communication
You will have an exclusive communication channel shared with our 24/7 operations team. Every query and report is immediately attended to.
Free browser plugin
You can check if we have flagged a site as dangerous and you can report a site to be taken down.
The Dashboard
Access to the place where we show all the information of every incident that we find. You can report incidents and download reports through it.
FAQs
Have some of the most asked questions answered:
Want to See PhishFort in Action?
See how PhishFort detects and eliminates digital threats across any digital space your brand has presence with a curated demo tailored to your organization's unique risk surface.